NZ Government Invests $8M To Keep Residents Safe
Share this: Click to share on Facebook (Opens in new window) Facebook Click to share on X (Opens in new window) X Like this:Like...
TLS Pages Used For Phishing
Share this: Click to share on Facebook (Opens in new window) Facebook Click to share on X (Opens in new window) X Like this:Like...
Mental Health App Are Sharing Your Data
Share this: Click to share on Facebook (Opens in new window) Facebook Click to share on X (Opens in new window) X Like this:Like...
Microsoft Support Agent’s Credentials Hacked
Share this: Click to share on Facebook (Opens in new window) Facebook Click to share on X (Opens in new window) X Like this:Like...
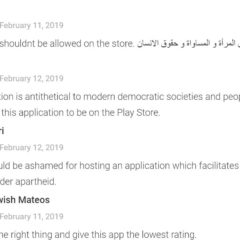
Are Google And Apple Hosting App which tracks women?
Share this: Click to share on Facebook (Opens in new window) Facebook Click to share on X (Opens in new window) X Like this:Like...